-
Security
-
-
AI Large Model
-
-
Cloud Phone
-
-
Solutions
-

Cloud Phone
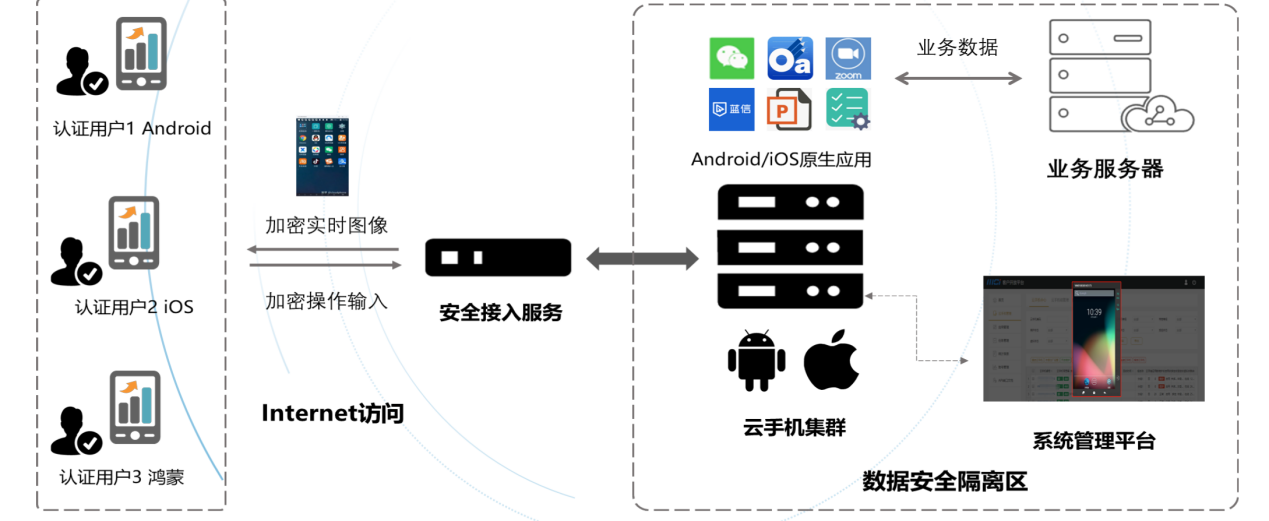
Users access the cloud phone through a cloud phone client with
security protection mechanisms, and use the application through
real-time encrypted video transmission and operation input. All
data interaction is executed within the cloud phone system in the
data isolation zone, and data does not leave the zone or land on
the terminal. The system management platform can comprehensively
manage and audit the application, data, and users. IOS cloud phone
servers use standard x86 servers, while Android cloud phones use
x86/Arm architecture servers.